Unlocking The Future: Mastering Security Remote Access IoT For Smarter Living
Hey there, tech-savvy readers! Ever wondered how your smart devices stay secure while connecting to the world? In today's interconnected era, the phrase "security remote access IoT" is more than just tech jargon—it's the backbone of our modern lifestyle. Imagine this: you're chilling at a café miles away from home, and suddenly you get a notification that someone is trying to access your smart thermostat. Sounds scary, right? But don’t panic! With the right strategies and tools, you can keep your IoT devices secure and enjoy peace of mind.
Now, let's break it down. IoT—or the Internet of Things—has revolutionized the way we interact with technology. From smart fridges to connected security cameras, these devices have become an integral part of our daily lives. However, with great power comes great responsibility. Ensuring that your IoT devices are protected from unauthorized access is crucial. This is where the concept of security remote access IoT comes into play.
But why should you care? Well, because the stakes are higher than ever. A recent study revealed that cyberattacks on IoT devices have surged by over 300% in the past year alone. That’s a massive red flag. So, if you're serious about safeguarding your digital fortress, you're in the right place. In this article, we'll dive deep into the world of IoT security and show you how to fortify your devices against potential threats.
- Jojo Horton Hears A Who A Whovian Adventure Thatrsquos Out Of This World
- Bongkrekic Acid Food Poisoning A Deep Dive Into The Silent Killer
Understanding the Basics of IoT Security
Let’s start with the fundamentals. IoT security refers to the measures taken to protect your smart devices from unauthorized access, data breaches, and other cyber threats. Think of it as a digital shield that keeps your personal information safe. Without proper security protocols, your IoT devices can become an easy target for hackers.
Here are a few key points to consider:
- IoT devices often lack robust built-in security features.
- Many users neglect basic security practices, such as changing default passwords.
- Network vulnerabilities can expose your devices to external threats.
So, how does remote access fit into this picture? Simply put, remote access allows you to control and monitor your IoT devices from anywhere in the world. While this convenience is a game-changer, it also introduces new security challenges. Ensuring that your remote access is secure is essential to maintaining the integrity of your IoT ecosystem.
- Unveiling The Mysteries Of Johnny From Hotel Transylvania The Ultimate Fan Guide
- Victor Reynolds Train Accident Nevada The Untold Story You Need To Hear
Why Security Remote Access IoT Matters
In a world where everything is connected, the importance of secure remote access cannot be overstated. Whether you're managing a smart home or overseeing an entire network of IoT devices, having a secure connection is vital. Here's why:
Firstly, remote access simplifies device management. You can check your security cameras, adjust your thermostat, or even lock your doors—all from the comfort of your couch. However, if this access isn't properly secured, it can become a gateway for cybercriminals. Imagine a scenario where a hacker gains access to your smart home system. The consequences could range from mere inconvenience to full-blown disaster.
Secondly, secure remote access enhances productivity. For businesses, IoT devices play a crucial role in streamlining operations. From monitoring inventory levels to tracking employee performance, these devices provide valuable insights. However, without proper security measures, sensitive data could fall into the wrong hands.
Common Threats to IoT Devices
Now that we've established why security remote access IoT is important, let's take a closer look at the threats your devices may face. Understanding these risks is the first step toward building a robust defense system.
- Data Breaches: Hackers can exploit vulnerabilities in your IoT devices to steal personal information.
- Malware Attacks: Malicious software can infect your devices, causing them to malfunction or send data to unauthorized parties.
- Man-in-the-Middle Attacks: These occur when a hacker intercepts communications between your devices and the network.
By staying informed about these threats, you can take proactive steps to protect your devices. Remember, knowledge is power!
Building a Secure IoT Ecosystem
So, how do you go about creating a secure IoT ecosystem? It all starts with implementing best practices for security remote access IoT. Here are some tips to get you started:
First and foremost, always change the default passwords on your devices. Many IoT devices come with generic login credentials that are easy for hackers to guess. By creating strong, unique passwords, you significantly reduce the risk of unauthorized access.
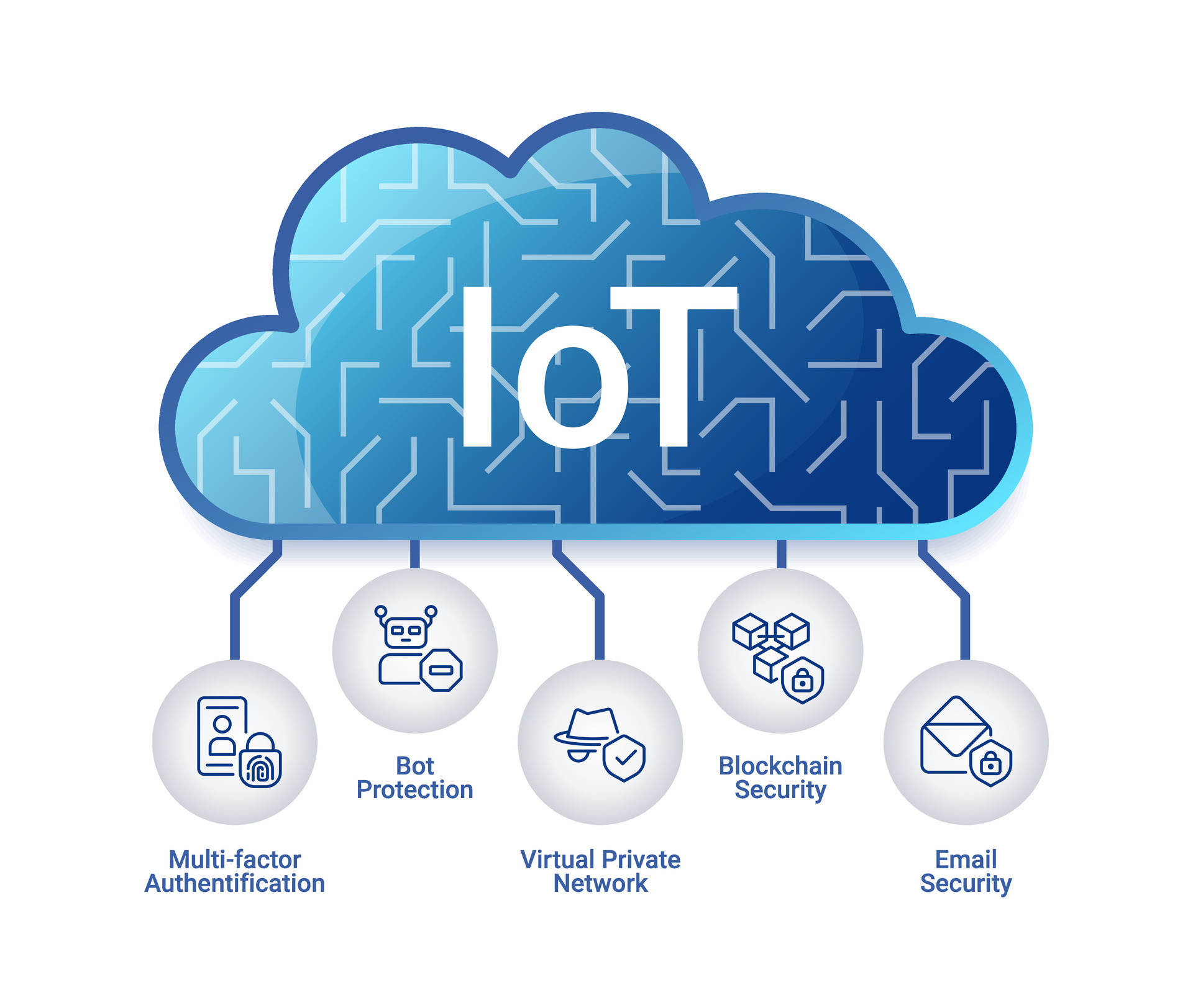
Next, consider using a Virtual Private Network (VPN). A VPN encrypts your internet connection, making it much harder for cybercriminals to intercept your data. This is especially important when accessing your IoT devices from public Wi-Fi networks.
Implementing Multi-Factor Authentication
Another effective way to enhance security is by enabling multi-factor authentication (MFA). MFA adds an extra layer of protection by requiring users to provide two or more verification factors before gaining access. For example, you might need to enter a password and then confirm your identity via a text message or fingerprint scan.
While MFA may seem like an extra step, it's a small price to pay for added security. In fact, studies have shown that MFA can prevent up to 99.9% of automated attacks.
Best Practices for Securing Remote Access
Securing remote access to your IoT devices involves more than just setting strong passwords. Here are some additional best practices to consider:
Regularly update your firmware and software. Manufacturers frequently release updates to fix known vulnerabilities. By keeping your devices up to date, you ensure that they're protected against the latest threats.
Limit access to trusted users only. If multiple people in your household or workplace use the same IoT network, consider creating separate user accounts with varying levels of access. This way, even if one account is compromised, the damage will be contained.
Monitoring and Logging
Implementing a monitoring system can help you detect suspicious activity on your network. By keeping an eye on login attempts, data transfers, and device behavior, you can quickly identify and respond to potential threats.
Additionally, maintaining detailed logs of all activity can be invaluable in the event of a security breach. These logs can provide valuable insights into how the breach occurred and help you prevent similar incidents in the future.
Tools and Technologies for IoT Security
When it comes to securing your IoT devices, having the right tools at your disposal can make all the difference. Here are a few technologies worth considering:
- Firewalls: A firewall acts as a barrier between your network and the outside world, blocking unauthorized access.
- Intrusion Detection Systems (IDS): An IDS monitors your network for suspicious activity and alerts you to potential threats.
- Encryption Software: Encryption ensures that your data remains private and secure, even if it's intercepted.
Investing in these tools can provide peace of mind and help you stay one step ahead of cybercriminals.
Choosing the Right Security Solutions
With so many security solutions available, choosing the right one can be overwhelming. To make an informed decision, consider the following factors:
- Compatibility with your existing devices and network.
- Level of customization and control offered.
- Customer support and reputation of the provider.
By evaluating these factors, you can find a solution that meets your specific needs and budget.
Real-World Examples of IoT Security Breaches
Let’s take a moment to examine some real-world examples of IoT security breaches. These cases highlight the importance of taking security seriously.
In 2016, the Mirai botnet attack targeted IoT devices, resulting in widespread internet outages. The attackers exploited weak passwords and outdated firmware to gain control of thousands of devices. This incident served as a wake-up call for many organizations, prompting them to reassess their security protocols.
Another notable example is the 2020 breach of a popular smart home platform. Hackers were able to access users' personal information, including names, email addresses, and even location data. This breach underscored the need for stronger data protection measures.
Lessons Learned
From these examples, we can draw several important lessons:
- Never underestimate the potential impact of a security breach.
- Regularly review and update your security measures to stay ahead of emerging threats.
- Stay informed about the latest developments in IoT security to better protect your devices.
By learning from these incidents, you can take proactive steps to safeguard your IoT ecosystem.
Future Trends in IoT Security
As technology continues to evolve, so too will the landscape of IoT security. Here are a few trends to watch out for:
Artificial intelligence (AI) and machine learning (ML) are increasingly being used to enhance security. These technologies can analyze vast amounts of data to detect patterns and anomalies that may indicate a security threat.
Blockchain technology is also gaining traction in the IoT space. By providing a decentralized and tamper-proof ledger, blockchain can help ensure the integrity of data transmitted between devices.
The Role of AI in IoT Security
AI has the potential to revolutionize IoT security by enabling predictive analytics and automated threat detection. For example, AI-powered systems can learn from past incidents to anticipate and prevent future attacks.
While AI offers many benefits, it's important to remember that no solution is foolproof. As cybercriminals become more sophisticated, so too must our security measures.
Conclusion: Take Action Today!
As we've explored in this article, security remote access IoT is a critical component of modern living. By understanding the risks and implementing best practices, you can protect your devices and enjoy the convenience of smart technology with confidence.
So, what's the next step? Start by reviewing your current security measures and identifying areas for improvement. Then, consider investing in the tools and technologies that will help you stay ahead of potential threats.
And don’t forget to share this article with your friends and family! The more people who understand the importance of IoT security, the safer we all become. Together, we can create a more secure and connected world. Stay safe, and happy tech-ing!
Table of Contents
- Understanding the Basics of IoT Security
- Why Security Remote Access IoT Matters
- Common Threats to IoT Devices
- Building a Secure IoT Ecosystem
- Best Practices for Securing Remote Access
- Tools and Technologies for IoT Security
- Real-World Examples of IoT Security Breaches
- Future Trends in IoT Security
- Conclusion: Take Action Today!
- Kordell Beckham Height The Rising Star Taking The World By Storm
- Dj Akademiks Net Worth How This Music Mogul Built His Empire

remote access iot by jamestylernew157 Issuu

IoT Security Securing Consumer IoT Devices
IoT Security SpyGuards Consulting LLC